Develop our organization (or organization of choice) Comprehensive Information and Security and Privacy Program
City University of New York- CUNY
Enterprise Security and Privacy Program
TABLE OF CONTENTS
1. BACKGROUND
2. PURPOSE
3. SCOPE
4. KEY TERMS AND DEFINITIONS
5. GOVERNANCE
6. REGULATORY LANDSCAPE
7. PRIVACY PROGRAM
8. DATA GOVERNANCE
9. TRAINING AND AWARENESS OF THE PROGRAM
10. RISK MANAGEMENT
11. RISK REGISTER
12. PHYSICAL SECURITY
13. POLICIES
14. PROCEDURES
15. GUIDELINES
16. TESTING
17. CONFIGURATION STANDARDS
18. CYBER DEFENSE PROGRAM
19. APPENDIX
20. SELF-REFLECTION ON THE OVERALL PLAN / PROGRAM
1. Background
CUNY stands for the City University of New York, which is a system of public colleges in New York City. CUNY's mission is to provide students with a high-quality education at an affordable price. CUNY includes both four-year colleges and community colleges. In total, the CUNY system offers more than 1,750-degree programs and 1,800 clubs.
CUNY schools’ range in competitiveness, with some having open admissions (where all applicants are accepted) to some four-years schools having acceptance rates below 40%.
Roughly 275,000 students attend a CUNY school on either a full-time or part-time basis, and the CUNY system is the largest comprehensive university system in the United States. It also has one of the most diverse student bodies in the country. CUNY consists of 25 undergraduate and graduate schools, located in all five boroughs.
Four-Year Colleges, Community Colleges, Graduate, Honors, and Professional Colleges
2. Purpose
This policy defines security requirements that apply to the information assets of the entire CUNY enterprise. Any unit of CUNY may, to meet its individual business needs or to satisfy specific legal requirements such as listed below exceed the security requirements instituted in this document; but all units must, at a minimum, achieve the security levels required by this policy.
Manage the risk of security exposure or compromise of CUNY information assets;
Designate responsibilities for the protection of CUNY information;
Optimize the integrity and reliability of CUNY information assets;
Reduce opportunities for the introduction of errors in information assets supporting CUNY business processes;
Promote and increase the awareness of information security at CUNY
3. Scope
This Policy establishes the authoritative information security and privacy policies that extend to all full-time and part-time CUNY employees, including faculty, administrative staff, temporary workers, interns, and student employees, as well as all other members of the CUNY community. Any information stored, accessed, or obtained by CUNY is protected by this program. Except in the case of personal information, this is not intended to replace any current CUNY regulation that includes more stringent standards for safeguarding those types of data.
Information security refers to the protection of information from accidental or unauthorized access, destruction, modification, or disclosure. Digital information is defined as the representation of facts, concepts, or instructions in a formalized manner suitable for communication, interpretation, or processing by computer-automated means. Digital information is relayed in a variety of methods, including through computer networks and portable media, such as jump drives, CD‟s and DVD‟s. Digital information is also stored and retrieved in several formats, including but not limited to computer databases or transmissions, tapes, computer-generated reports, hard copy documentation, e-mail messages, and voice mail.
This policy must be communicated by supervisors to all employees and all others who have access to or manage CUNY digital information. This security policy is technology independent and does not include implementation standards, processes, or procedures.
4. Key Terms and Definitions
Confidentiality, Integrity, and Availability (CIA) are incorporated into the policies, procedures, and standards of CUNY.
Confidentially: CUNY confidentiality refers to data being accessible only by the intended individual or party.
Measures used at CUNY to improve confidentiality may include:
Training
Sensitive data handling and disposal
Physical access control
Storing personal documents in locked cabinets
Logical access control
User IDs, passwords, and two-factor authentication
Integrity: At CUNY integrity mean preventing unauthorized individuals from modifying the data and ensuring the data’s consistency and accuracy over its entire life cycle. Specific scenarios may require data integrity but not confidentiality. For example, if you are downloading a piece of software from the Internet, you may wish to ensure that the installation package has not been tampered with by a third party to include malicious code.
Use of file permissions
Limit access to read-only
Availability: Availability at CUNY refers to ensuring that data is available to authorized individuals when required. Data only has value if it is accessible at the required moment. A common form of attack on availability is a Denial of Service (DoS) which prevents authorized individuals from accessing the required data. You may be aware of the recent ransomware attack on CUNY. This was a DoS attack as it prevented users from being able to access their own files and requested a ransom in exchange for reinstating that access.
Access Control List: is a set of rules that is used against unauthorized access.
Inherent Risk: it is the threat that occurs before any countermeasures are implemented to minimize or eliminate the risk.
Residual Risk: it is the threat that remains after a company has taken all necessary precautions.
Threat: a threat is what we’re trying to protect against.
Vulnerability: a vulnerability is a flaw or weakness in our security measures.
Virtual Private Network: a VPN is a tool that helps us to hide our IP address and ensure safety online.
Ransomware: is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable.
5. Governance
Under what authority is this program manual? CEO / Board? Both? Has the CEO delegated the authority to anyone internally? Who is responsible for carrying out this program? What groups need to be informed of this program in order for it to be fully effective (hint – risk/privacy management applies to all areas of the business in some way or another)?
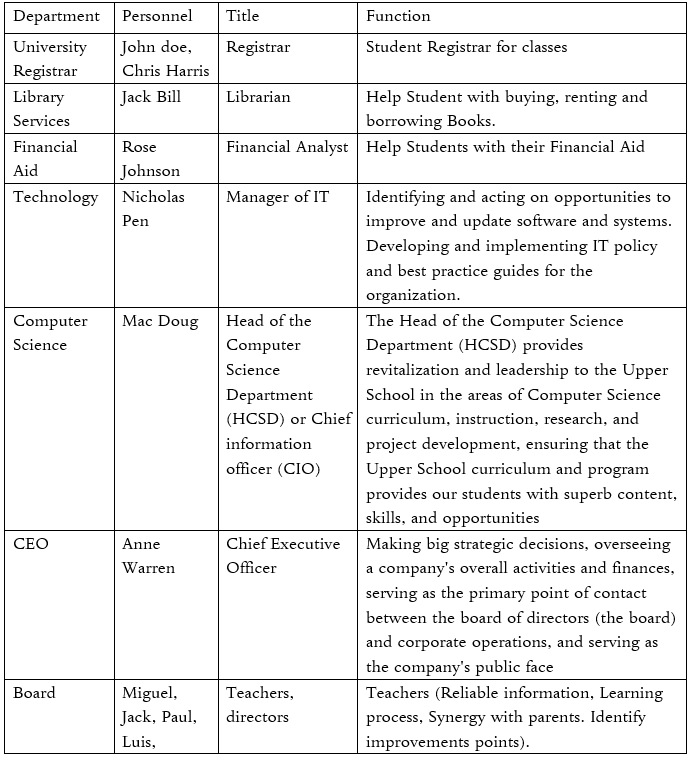
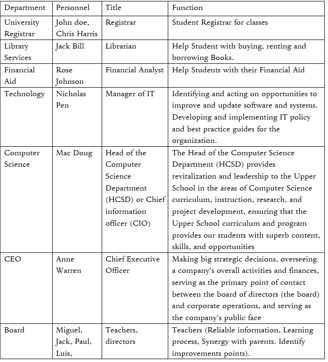
All stakeholders will be represented on the council, which will meet every Friday to discuss the school's weaknesses, risks, and protection, as well as how all of this can be improved. Whenever the CUNY protection and privacy policy are updated, all Board members must offer their approval in a meeting before the policy can be implemented. The CEO will assign the job to the heads of each department after granting permission to amend the policy, and the heads of each department will remind any new employee about the new policy.
Enforcement
You can more easily implement risk-based, context-aware rules once you've created an authoritative identity source and established risk-based, context-aware rules within your automated tool. Intelligent analytics will automatically compare access requests to policies, submit potential violation warnings, and recommend remediation measures, allowing you to reduce operational and enforcement risks. The standards for systems and applications are enforced by this regulation. Although it's important to think about encrypting or password-protecting individual files or documents, particularly if they'll be submitted electronically or stored on a portable device, the policy's goal isn't to make those requirements.
Other Responsibility and Accountability
The Information Systems Team is responsible to maintain all devices and applications for CUNY members. They are also responsible for implementing and managing security or integrity and backup procedures.
6. Regulatory Landscape
Regulators
US Department of Education
CUNY
Regulations
Family Educational Rights and Privacy Act (FERPA); Environmental Health, Safety, and Risk Management (EHSRM), and Health Insurance Portability and Accountability Act (HIPPA).
The first step in pursuit of this mission is to ensure that CUNY follows applicable regulations and University policies and procedures. In addition to completing a five-year EPA audit and disclosure program, EHSRM continues to build an integrated CUNY-wide environmental, health, safety, and risk management system. This includes coordinating and organizing programs that minimize individual and institutional risk, alleviate environmental impact and protect the health and safety of the CUNY community.
7. Privacy Program
Privacy of an individual’s information must be respected throughout its lifetime.
The protection of the privacy of personal information is of utmost importance and CUNY must conduct business so as to protect the rights of privacy of all members of the public, business partners, and CUNY community.
All CUNY employees with access to personal information are required to respect the confidentiality of that personal information.
Personal data, including information about students, employees, members of the public, organizations, and business partners, collected and maintained by CUNY must:
Be used only for the stated purpose for which it was gathered;
Be gathered in lawful and fair circumstances;
Be kept for the amount of time required by law or regulations or as long as it remains relevant for its primary purpose;
Not be disclosed without specific consent or as authorized by law;
Be available for review by authorized individuals;
Be corrected if errors are known to exist or if the individual identifies errors;
8. Data Governance
Our University implemented a system called: The AAA Framework is a simple way to understand security issues surrounding the access ability of individuals within an organization,
Authenticate: confirm the right person is accessing the system
Authorize: Give minimum access to their needs
Accounting: Monitor activities for security and compliance
Our organization also uses a protocol called RADIUS and these protocols put these elements together into a package to help manage the elements of identity security for our organizations. RADIUS, which stands for remote Authentication Dial-In User Service, RADIUS is an open protocol that provides access for users trying to connect to a network, authorization for records, and accounting of the usage.
9. Training and Awareness of the Program
Chief Information Security Officer (CISO) should:
Develop, enforce, and maintain a robust training and awareness plan to ensure that employees are respectful of their privacy rights and responsibilities.
Include basic privacy training for all employees on an annual basis, as well as role-based privacy training that includes cybersecurity tabletop exercises.
Ensure that staff assumes responsibility for privacy standards on an annual basis, which includes designing curriculum and providing instruction.
Our training and awareness of the program have the most efficient way to educate our employees on how to fortify the human element of our University’s security through cybersecurity awareness training. During our cybersecurity awareness training, our CUNY employees will learn about various attacks and how to prevent and protect themselves against these attacks. Some of these attacks are phishing, social engineering, compromised and weak network security, zero-day exploits, ransomware, vishing, etc.
10. Risk Management
Our university will be using the NIST CFS Framework to improve our infrastructure. The National Institute of Standards and Technology (NIST) Cybersecurity System (NIST CSF) is a policy for private sector organizations to evaluate and develop their ability to avoid, track, and respond to cyber-attacks. The NIST Cybersecurity aims to address the lack of security requirements. There are significant differences in how businesses combat hackers, data pirates, and ransomware using systems, languages, and rules. The framework is divided into three parts, "Core", "Profile" and "Tiers". The "Framework Core" contains an array of activities, outcomes, and references that detail approaches to aspects of cyber security. An organization's "Framework Implementation Tiers" are used to explain how it defines cybersecurity risk and the sophistication of its management strategy towards itself and its partners. Finally, a "Framework Profile" is a list of outcomes selected by a company from the various categories and subcategories, based on its business needs and individual risk assessments. In order to access the maturity of our cybersecurity program we chose to use an assessment methodology based on the NIST categories. NIST assesses our program in these 5 key areas:
Identify: Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Protect: Develop and implement the appropriate safeguards to ensure the delivery of critical infrastructure services.
Detect: Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond: Develop and implement the appropriate activities to act regarding a detected cybersecurity event.
Recover: Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
The methodology used to conduct the evaluation is written policy (Amazon has a written policy incorporated into the recovery plans), risk management (Risk management processes are managed and agreed to by organizational stakeholders), Awareness, and training. To mitigate the risk, the company has several documents for its faculty to implement, like well-written guidelines, community policy, and password policy.
Assess risk on a likelihood scale designates a risk into different levels or chances of occurrence of a risk. It can be given a value of 1 to 5 with increasing order of severity.
11. Risk Register
CUNY risk register is a centralized inventory, often a spreadsheet of risks that an organization identifies in its environment while performing risk management or assessment activities. Our risk register includes a description of the risk, an estimate of the impact, the likelihood, risk rating, and any mitigating controls.
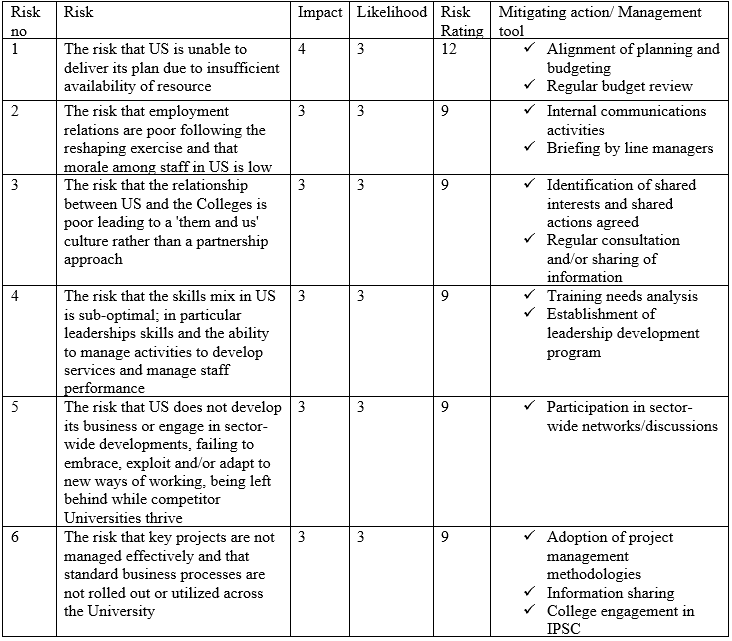
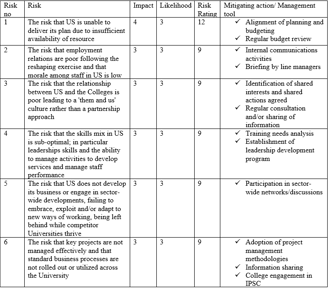
12. Physical Security
To take steps to ensure that these tools cannot be tampered with or stolen physically. The following are some of these measures:
Locked doors and physical intrusion detection
Access control, Fire safety
Secure equipment: To keep devices from being stolen, they should be locked down. Since one employee's hard drive could contain all of your customer data, it's important that it's kept secure.
Both servers and other high-value equipment should be stored in a room that is constantly monitored for temperature, humidity, and airflow to avoid the possibility of a server failure if these variables fall outside of a set range.
Records should be categorized into record types, such as accounting records, database records, transaction logs audit logs, and operational procedures, each with details of retention periods and type of storage media, e.g. paper, microfiche, magnetic, and optical. Any related cryptographic keys associated with encrypted archives or digital signatures should be kept securely and made available to authorized persons when needed.
13. Policies
Data Classification and Governance Policy
This policy is intended to reassure teachers, employees, and students that their personal data will be kept private and confidential in accordance with school policy and all applicable state and federal laws and regulations.
Identify and Access Management Policy
Everyone who has access to CUNY systems is responsible for choosing strong passwords, keeping them safe, and reporting any unauthorized account use. Users must comply with the following requirements:
Create passwords that follow best practices for password selection, such as length and complexity.
Do not give out passwords to any University system to someone else.
Do not use any college-related passwords for non-college accounts.
If there is reason to suspect that a password has been inappropriately disclosed, obtained, or used by an unauthorized user, modify it immediately and notify the responsible system administrator and/or Information Security.
Only use account privileges for the reason for which they were granted, and nothing else.
Data Retention and Destruction Policy
Regardless of the method of storage, dispose of, delete, remove, and/or anonymize the data.
Website Privacy Policy and Terms of Use
The most extensive and flexible privacy generator tool available would be covered by the website's Privacy Policy and Terms of Use. The following are some of the topics covered:
Website
Personally, Identifying Information
Security
Advertisements
External Links
Cookies
Mobile Device Policy
This policy extends to all CUNY employees who use personal or company-issued mobile computing devices for work.
Mobile computing systems must have a password that must be entered when the computer is turned on.
The CUNY Access Control and Password Policy specifies the specifications for passwords.
Encryption is required for all data stored on mobile devices.
CUNY also implemented BYOD. Bring-your-own-device (BYOD) policies are set by CUNY to allow employees to use their personal smartphones, laptops, and tablets for work.
Acceptable Use Policy
An acceptable use policy helps reduce risk when it comes to online safety, decreased productivity, and damage to both the company and the users. The following are some Acceptable Use policies:
Ensure the safety of the users
Protect the online business from any legal action
Rights and responsibilities of the user
Enhance ease of use and productivity
14. Procedures
Business Recovery Procedures
It is important to have a business recovery procedures plan in order to ensure the company's continued success. Any business maintains a permanent business recovery team that focuses on the disaster. The ICT or IS teams may receive the information they need to rebuild their processes in order to execute the IT Service Continuity Plan.
Disaster Recovery Procedures
The following are the emergency response procedures:
Record the proper emergency response to a fire, natural disaster, or other activity in order to save lives and minimize property damage.
Procedures for backup operations
To ensure that critical data processing operations can resume following the outage.
Procedures for regaining control
Information services backup procedures
Inventory profile
Incident Response Procedures
Develop and execute a Privacy Incident Response Plan; and Respond to privacy incidents in a systematic and efficient manner in compliance with the organization's Privacy Incident Procedure for Responding to Breaches of Personally Identifiable Information.
Identity and Access Management Procedures
The identity and Access Management Policy is to establish the requirements necessary to ensure access to and use of Information Resources. Here are seven identity management best practices you should be following as you develop your Identity and Access Management (IAM) strategy.
Begin with the end in mind
Eliminate High-Risk Systems
Routine Review and Removal of Orphaned Accounts
Automate Onboarding and Offboarding
Develop a Zero Trust Approach to Security
Use Multi-factor Authentication
Centralize Your System
Third-Party / Supply Chain Due Diligence Procedures
Ensure objectivity and continuity in due diligence attempts to minimize the risk of human error or misconduct.
Only share PII with third parties for the purposes allowed by the Privacy Act, as defined in its notice(s), and for a use that is consistent with those collections.
Computer Matching Agreements or similar agreements with third parties that detail the PII protected and the purposes for which the shared or distributed PII may be used
Track, inspect, and train its employees on the permitted sharing of personal information with third parties, as well as the effects of unauthorized use or sharing of personal information.
Examine any potential new instances of sharing PII with third parties to see if they are approved and if additional or new public notification is needed.
Identify and access high-risk areas that need focus
Software Development Lifecycle Procedures
The Software Development Lifecycle Procedures at CUNY are planning, analysis, design, building, testing, deployment, and maintenance. Also, the team will deal with cybersecurity basics using Agile Blue Team Procedures:
Cyber security analysts (scanning, pen testing/ etc.)
Cyber Engineers (Patch/Remediate/ etc.)
Cyber Architects (Chef – Security by Design)
Scrum Master / Retrospectives (Cyber Project Manager)
Owners of Cyber Application/Process
15. Guidelines
Data Loss Prevention Guidelines
Data loss prevention Guidelines can help CUNY prevent unauthorized data access and protect itself from potential damage. These are some Guidelines examples:
Identify and classify sensitive data
Use data encryption
Harden your systems.
Implement a rigorous patch management strategy.
Allocate roles.
Automate as much as possible.
Use anomaly detection.
Educate stakeholders.
Physical Security Guidelines
Organize working groups and work through existing councils to identify and establish procedures and other areas of change that may be instituted to further protect the integrity of University files and systems.
Additional and/or revised procedural statements may be adopted from time to time and introduced for University compliance. Further procedural documents may be developed to elaborate detail on these IT Security Procedures, but they will in no way detract or suggest a different level of compliance that is expected or required.
Non-compliance with these IT Security Procedures may result in termination of access to the University network and applications until such time that compliance is re-established. Non-compliance may also result in disciplinary action.
Inventory and Asset Management Guidelines
College and Central Office management are responsible for maintaining and overseeing compliance with these IT Security Procedures within their line responsibilities.
Vulnerability Management
CUNY vulnerability posture is monitored by the Security Team, which manages the vulnerability management solution, produces reports, and maintains the company's vulnerability posture. The team makes sure that systems are scanned for vulnerabilities on a regular basis and that any vulnerabilities discovered are reported to the appropriate people.
16. Testing
Annual Risk Assessments
The aim of the annual risk assessment process is to evaluate hazards, then remove that hazard or minimize the level of its risk by adding control measures, as necessary. By doing so, you have created a safer and healthier workplace. At CUNY risk assessments are very important as they form an integral part of an occupational health and safety management plan. They help to:
Create awareness of hazards and risks.
Identify who may be at risk (employees, cleaners, visitors, contractors, the public, students, etc.).
Determine whether a control program is required for a particular hazard.
Determine if existing control measures are adequate or if more should be done.
Prioritize hazards and control measures.
Meet legal requirements where applicable.
Annual Penetration Testing
Annual Penetration Testing simulates a cyber-attack on your computer system in order to find exploitable flaws. Penetration testing is often used to supplement a web application firewall in the sense of web application protection (WAF). Our Pen tester team entails attempts to break through a variety of application frameworks (frontend/backend servers) in order to find bugs, such as unsanitized inputs that are vulnerable to code injection attacks. The penetration test's findings can be used to fine-tune your WAF security policies and fix discovered vulnerabilities.
Annual DR/BCP Testing
Annual DR/BCP Testing ensures the continuity of our business operations in case of a cyber-attack or disaster. Regardless of the size of our organization, we aim to continue to remain competitive. The only way to ensure this is through solid DR/BCP testing.
Technically at CUNY, the Disaster Recovery (DRP) deals with the restoration of computer systems with all attendant software and connections to full functionality under a variety of damaging or interfering external conditions. In daily practice, Business Continuity often refers to disaster recovery from a business point-of-view, or dealing with simple daily issues, such as a failed disk, failed server or database, and possibly a bad communications line.
Periodic Phishing Testing
CUNY sends out deceptive emails that look like malicious emails to its own employees to see how they respond to phishing and other email attacks. Employees who fail the CUNY phishing test on a regular basis can pose a risk to the university. It is important to educate all staff on the importance of cybersecurity awareness.
17. Configuration Standards
Mobile Device Configuration Standards (Mobile Device Management)
This procedure applies to CUNY, departments, employees (student employees included), and faculty members, where mobile computing devices are used to store process, or access university information. If the university provides these devices to the employee or department, the configuration standards are mandatory. Equipment such as laptops, tablet PCs, and mini-notebooks, is considered a separate class of computing equipment and is not in the scope of this procedure.
Desktop / Laptop Configuration Standards
Desktop / Laptop Configuration Standards are really important at CUNY, without them the Computers will be vulnerable. The Standard Desktop/Laptop at CUNY is a specific configuration within a network environment for personal computers in a local area network that provides all PCs with the same level of protection. It will include security measures built into Windows such as Windows Firewall, VPN, and Anti-virus.
Network Device Configuration Standards
Network device configuration standards make up the campus's wired and wireless infrastructure. It is critical that those devices are secure and available at all times. By following CUNY Information Technology Resources Program, campus network security, and availability will be maximized. By auditing network control device configurations on a recurring basis, we are decreasing the chance that a device will be compromised or fail due to configuration errors. For the purposes of this document, network device configuration standards include but are not limited to switches, routers, firewalls, and wireless networking equipment.
Network Security Standards
Network security standards are focused on ensuring three security objectives of information technology systems: confidentiality, integrity, and availability. CUNY uses the NIST Framework to manage and mitigate cybersecurity risk.
Email Configuration Standards (incoming/outgoing / mail client)
When configuring email on any mail client/ incoming/ outgoing, we'll need to know specific information in order to create the account. The most basic information we'll need to know is:
Username
Password
Mail server name
We can then configure our email user further by setting it up as an IMAP, SMTP, or POP address and enabling secure ports. This is are the steps you will need to take to configure an email made at CUNY:
Step 1 — Add the email address to the panel
Step 2 — Locate your username and password
Step 3 — Locate your mail server name
Step 4 — Set secure ports and choose IMAP or POP
18. Cyber Defense Program
The most appealing cyber security solution in our organization would be Agile security, the three lines of Defense, both defense-in-depth and zero trust architecture. Agile security is essentially the proposal to engage in new software that takes the core principles of agile development. This is scalable software and repeatable development. This goes hand in hand with moving target defense cybersecurity technologies. The agile approach differs for a few reasons but first, there are 7 core principles and the traditional line of defense has 3 models. One of the differences between agile defense is different is from two of the main things which are minimalism and repeatability. Minimalism will say only run-on programs and software that you need and not anything else. The Repeatability principle examines the idea that automating as many things as you can with being precise as possible with it. “Run what you know and only what you know.” Back then it would take a long time to update a cloud service. Now it’s much quicker. The three lines of defense focus on internal audit, risk compliance, and IT governance and control. These are different approaches, to say the least. Another difference between agile and traditional lines of defense is that it is more critical for the achievement of organizational objectives. I tend to agree with both approaches. There are some that would say that the three lines of defense are outdated but it has worked and still works to this day. Both are trying to be more effective and reliable and collaborations would ultimately help both of the objectives. The agile method or approach focuses on the culture like how individuals work together, trying to figure out how to better code, or create features that help. Agile stays away from governance but instead, it forces a shift in the way that developers see individuals, technology, and process.
To reduce the attack surface from the viewpoint of outsiders, we must introduce several layers of protection mechanisms. We need to add many layers of defense mechanisms to reduce the attack surface from the perspective of outsiders. To help minimize any harm to the device, we must continue to improve our tactical defense strategy. Defense in depth is a data and information security strategy that consists of several layers of protective mechanisms. If one layer fails to avoid the attack, a second layer will be deployed to stop the attack right away. The aim of the multi-layered approach is to add intentional redundancies to the system's security. As a result, it will be able to deal with a wide range of attack vectors. Zero Trust is a strategic initiative that helps prevent successful data breaches by eliminating the concept of trust from an organization’s network architecture. Rooted in the principle of “never trust, always verify,” Zero Trust is designed to protect modern digital environments by leveraging network segmentation, preventing lateral movement, providing Layer 7 threat prevention, and simplifying granular user-access control. The only thing they have in common is that they are both built to defend their systems from malicious actors. The aim of protection in depth is to secure the system by putting in place multiple layers of defense mechanisms while still trusting insiders. The zero-Trust architecture, on the other hand, is designed to secure the system by not trusting anybody, even insiders. It just allows them to do their job with the bare minimum of permission.
19. Appendix
CUNY City University of New York
PII Personally Identifiable Information
ACL Access Control List
EHSRM Environmental Health, Safety, and Risk Management
EPA audit Environmental Auditing Policy
IPsec Internet Protocol Security
CISO Chief Information Security Officer
FERPA Family Educational Rights and Privacy Act
NIST National Institute of Standards and Technology