DFIR Project
You are working as a forensic/incident response investigator for Iridium Electronics and have been asked to investigate in a case of suspected data theft/employee misconduct. The company’s management team have been concerned of late because they have not been receiving any client responses to quotes that have been sent out by Jen Barber, an employee at the company whose supervisor is Douglas Reynholm, the company’s Chief Financial Officer. Without the business generated by those quotes, the company is at serious risk of financial failure and bankruptcy. After a brief preliminary investigation, suspicions have fallen on Richmond Avenal, an employee under Barber who was recently terminated for poor performance and attitude.
Shortly after Avenal was terminated, Barber alerted a member of the IT Security team (Roy Trenneman) to state that she believed that her computer was being operated remotely using a remote control application called “TeamViewer”. Although she could not prove it conclusively, she believed that Avenal was behind this activity based on a TeamViewer dialog that she saw on her screen. The attacker appeared to be trying to email confidential quotes to an employee of a competing company called “Goth2Boss”. Barber further stated that Avenal had earlier told her that TeamViewer had been installed for the purposes of IT support. Barber further stated that her password (“Dora&Gwen”) were the names of her children (whom she often talks about at work with her colleagues) and hadn’t been changed since she joined the company years ago.
Avenal and Barber’s Windows 10 workstations (IRRIDIUM-AVENAL and IRRIDIUM-BARBER) were joined to the Microsoft Windows domain Irridium.local which has a single Windows domain controller (IRRIDIUM-DC). The static internal IP address of IRRIDIUM-DC is 192.168.0.1
Based on these facts, the IT security staff have done the following:
Used EnCase Enterprise to take volatile data “snapshots” of both workstations
Took screenshots of both workstations.
Acquired the RAM from both Barber and Avenal workstations (this analysis is optional for the Final Project but you can attempt to analyze the sample with the Volatility software if you wish).
Powered off both machines and imaged the drives
Acquired a JetFlash USB drive that was turned over by Barber
Acquired a SanDisk Cruzer Micro USB drive which had been found in a locked drawer in Avenal’s old desk.
Performed a logical acquisition on IRRIDUM-DC of the mail database from the hMailServer mail-server application and an “administrative” EFS recover key (Roy shared the File Recovery Key password “TryReb00ting”) along with group policy reports showing, amongst other things, recovery keys for two BitLocker volumes on Avenal’s workstation.
Uploaded all the evidence into a secure evidence server.
Please perform the following:
Download the images onto an evidence storage drive (i.e. an external USB drive)
Complete a COC for the receptacle drive and evidence inventory for the image
Calculate the MD5 and SHA1 hash values for the image
Find any and all evidence about the alleged data theft/unauthorized host intrusion, and any unlawful activities performed by Avenal before he was fired.
Please document any findings you make in a complete investigative report (please assume that your audience has little to no technical background in digital forensics). Please include the following items in your report:
Title Page
Table of Contents
Request
Executive Summary
Collection Summary
Investigation Report
Conclusion
Timeline of Events
References
Exhibits (if necessary)
Note that any relevant files found should be saved as separate report exhibits to be included at the end of the report after the conclusion.
INVESTIGATION REPORT
Prepared for:
IRIDIUM ELECTRONIC’S CORPORATE
CASE NUMBER
# 08
January 5th , 2017
Prepared by:
Ismael Belem
Digital Forensic & Incident Response Investigator
TABLE OF CONTENTS
INVESTIGATION REPORT
REQUEST
EXECUTIVE SUMMARY
COLLECTION SUMMARY
INVESTIGATION REPORT
CONCLUSION
TIMELINE Of EVENTS
LIST OF TOOLS USED
REFERENCES
REQUEST
The company where we work (Iridium Electronics) ordered one of their Digital Forensic & Incident Response investigators to investigate into a case of suspected data theft/employee misconduct in November 2016.
Our forensic team was also tasked with locating any and all evidence related to the claimed data theft/ unauthorized host access, as well as any illegal conduct committed by Avenal prior to his termination.
EXECUTIVE SUMMARY
The management team at Iridium Electronics has been concerned recently because they have not received any client answers to quotes sent out by Jen Barber, a company employee whose supervisor is Douglas Reynholm, the company's Chief Financial Officer. The company is at great risk of financial disaster and insolvency if those quotes do not generate revenue. Richmond Avenal, a Barber employee who was recently terminated for poor performance and attitude, has been named as the subject of accusations following a preliminary investigation.
Barber informed a member of the IT Security team (Roy Trenneman) shortly after Avenal's termination that she suspected her computer was being controlled remotely via a remote-control application called "TeamViewer." She suspected Avenal was behind this action based on a TeamViewer dialog she saw on her screen, albeit she couldn't confirm it conclusively. The attacker looked to be attempting to communicate secret quotes to a competitor named "Goth2Boss" employee. Barber went on to say that Avenal had previously told her that TeamViewer had been deployed for IT support. Barber went on to say that her password ("Dora&Gwen") was the names of her daughters (whom she frequently discusses at work with her coworkers) and that she hadn't changed it since she started working there years ago.
The Windows 10 workstations of Avenal and Barber (IRRIDIUM-AVENAL and IRRIDIUM- BARBER) were linked to the Irridium.local Microsoft Windows domain, which has a single Windows domain controller (IRRIDIUM-DC). IRRIDIUM-DC has a static internal IP address of 192.168.0.1.
Our department performed a forensics analysis on the evidence files (IRRIDIUM-AVENAL, IRRIDIUM-BARBER, RAM Analysis, Screenshots, Snapshots, BARBER Jetflash 1GB.E01, AVENAL SanDisk Cruzer Micro.E01). The analysis of the collected evidence determined:
Analyses of snapshots
We discovered that Avenal Workstation made a remote connection with Jen Barber's Workstation by evaluating the open ports 49714. Because Avenal's workstation IP address is 192.168.0.22 and Jen Barber's workstation IP address is 192.168.0.21, we were able to come to a conclusion.
According to the snapshots, a TCP connection was established on Avenal Workstation using port 5938. (TeamViewer port number). On the snapshot, we can also observe that Avenal's IP address established a connection with the IP addresses 188.172.219.35 and 37.252.231.5.
On Barber workstation, we can see that a connection was established using TeamViewer.
Analysis of the Screenshots take shows that:
A recovery password was kept on IRRIDIUM-Avenal on IRRIDIUM-DC, and this recovery password was used to access the Avenal-encrypted vhd files.
The team was able to capture a good picture of the Accounts names as well as Jen.Barber data using HmailServerAdministration.
We can see on IRRIDIUM-BARBER that Richmond Avenal -PC (976 00391) used a remote connection to connect to Barber's computer and then sent an email to Vince Black (employee at goth2boss at 11:53). Richmond sends the private data using the email address dark628837@gmail.com.
The pictures on IRRIDIUM-Avenal reveal that Avenal has access to Jen.PC Barber's without her knowledge. He then downloads the files as VHD files and sends them to himself.
IRRIDIUM-BARBER Analysis shows:
We can view all of the files related to the machine on IRRIDIUM-BARBER.E01 (img_IRRIDIUM-BARBER.E01/vol_vol3/Users/jen.barber/Documents/Quotes), and by opening these files, we can see that Jen Barber sent out those quotations to the clients, but no responses were received.
The IP address 192.168.0.22(unauthorize/anonymous login) had access to Barber Computer, according to Microsoft-Windows-SMBserver found in / IRRIDIUM- BARBER.E01/vol vol3/windows/System32/winevt/Logs.
On Barber's machine, Microsoft-windows-TerminalServices-RemoteConnectMangere revealed the same IP address 192.168.0.22.
UserName
NT AUTHORITYANONYMOUS LOGON
192.168.0.22
Whilst also looking at the folder prefetch view on Barber machines, we were able to figure out when Team Viewer was last used, as well as the date and time. All of the information found is listed below, and it proves that Avenal visited Barber's computer at the time specified.
IRRIDIUM-AVENAL Analysis shows:
Analyzing Avenal's Prefetch data reveals that he used TeamViewer to control Barber's computer because Avenal had access to Barber on the same day and time
We were able to see that Richmond.Avenal accessed a computer using remotecontrol on the 9/10/2015 from 14:18:12 to 17:22:03 and the 10/10/2015 from 10/10/2015 to 12:55:58 by analyzing the TeamViewer folder on IRRIDIUM-AVENAL.E01, specifically the folder Teamviewer.
We discovered that Richmond.avenal saved the stuff.vhd to a document folder and also downloaded confidential files that he wasn't supposed to see. These files can be found at /img_IRRIDIUM- AVENAL.E01/vol_vol3/Users/richmond.avenal/AppData/Roaming/Microsoft/Office/Recent
We were able to access the vhd files saved on Iridium-Avenal by utilizing the application Asernal Image and the evidence (screenshot of the Active Directory) as well as the Recovery password " 594858-179674-652850-618948-667656-268378-541156-660748" to unlock. On October 8th, 2015, and October 14th, 2015, the confidential quotes were downloaded on Avenal's computer. The Bitlocker recovery keys were saved on the folder name private in the directory documents.
We can observe that the TeamViewer_Setup_en was downloaded on 10/08/2015 at 5:48 am by checking the folder installers. We suspect that TeamViewer was first installed and then used to obtain access to Barber's computer so that the secret information could be downloaded. The first quotations files were downloaded at 9:01 a.m. on October 8, 2015, and the second quotes folders were downloaded at 7:40 a.m. on October 14, 2015.
We also found that the files that were downloaded were in Word and pdf
Quotes Downloaded October 8th, 2015
Flower-Power Holdings In- October 2nd , 2015 at 10:04AM
Fraggle Inc.-October 2nd, 2015 at 4:35 AM
Jenson Enterprises- October 2nd, 2015 at 9:55 AM
Weyland-Yutani – October 5th, 2015 at 5:59 AM Quotes Downloaded October 14th, 2015
Border Holdings Inc.- October 9th, 2015 at 12:04 PM
Chewbacca Entertainment Co.- October 9th, 2015 at 12:29 PM
On 2015-10-02 05:57:25 EDT, we were able to notice that Avenal's flash drive was attached on Avenal's workstation.
Analysis of Ram
Following the vhd, we continue our analysis by examining the Avenal and Barber Ram. We believe they were not processing background on Barber's computer, but we can see that Avenal was using TeamViewer on 2015-10-14 from 11:24:59 UTC to 11:35:55 UTC on Avenal's PC. Avenal was most likely using TeamViewer to gain access to the victim's PC in order to gain control and steal data.
IRRIDIUM-DC Logical acq.L01
By looking through the carvedfiles, we realized that Richmond Avenal texted Jen. He wanted to know how she handled the confidential documents. He also volunteered to help her complete the quotes. Jen replied to Richmond's email by telling him that the quotes were very confidential and that he wasn't allowed to see them. It was suspicious that Avenal was attempting to read the message. He was acting as if he had no intention of seeing or stealing this material.
Avenal also informed Jean that Roy had instructed them to leave their computer at work because he needed to update it with a security update.
Avenal told Barber that the IT Team was installing TeamViewer, while she was out.
SanDisk U3 Cruzer Micro USB Device Analysis shows:
SanDisk U3 Cruzer Micro USB Device was encrypted by BitLockerToGo, and we were able to unlock it by using the recovery key (077407436876003740453519387629611215416295162514) that was provided by IT Security Staff. The encrypted USB Device contains two folders as follows:
Installers folder contains Eraser 6.2.0.2970.exe, filedatech.zip, SDelete.zip, and TeamViewer_Setup_en.exe.
The private folder contains two BitLocker Recover Keys, SDelete Info.pdf and TV Firewall Info.pdf.
The private folder was encrypted by encrypting file system (EFS). We managed to unlock the folder by installing a digital certificate named Roy Trenneman - File Recovery Key.pfx extracted from the IRRIDIUM-DC Logical Acq.L01 image and installed the digital certificate on our forensic machine with the password “TryReb00ting” shared by Roy (IT security team).
· The user was trying to learn how to delete files in an unrecoverable way.
JetFlash USB drive Analysis shows:
Nothing suspicious on the USB device. The images taken during the Vatican trip were all kept on the JetFlash USB disk.
COLLECTION SUMMARY
IT security staff gathered each piece of evidence, which was subsequently imaged and sent to our server. The following are the verification summaries for each computer scanned by our Lab using Encase Enterprise, autopsy 4.18.0
Name: /img_IRRIDIUM-AVENAL.E01
Type: E01
Size (Bytes): 64424509440
MD5: f9bb6e91a4efa64aa178e054672409ef
Sector Size: 512
Time Zone: America/New_York Acquisition Details
Description: IRRIDIUM-AVENAL
Evidence Number: IRRIDIUM-AVENAL
Examiner Name: delme
Acquired Date: Tue Nov 1 00:03:42 2016
Name: /img_IRRIDIUM-BARBER.E01
Type: E01
Size: 64424509440
MD5: 4f9b30ba64f69731cebbfbf4fda4bd51
Sector Size: 512
Time Zone: America/New_York Acquisition Details
Description: IRRIDIUM-BARBER
Evidence Number: IRRIDIUM-BARBER
Examiner Name: delme
Acquired Date: Tue Nov 1 00:52:55 2016
System Date: Wed Oct 14 13:59:42 2015 Acquiry Operating System: Windows 10 Acquiry Software Version: 8.01.00.50
Device ID: 36ce409e-9bb7-4f82-af93-c2aaa727dffe
Name: /img_BARBER JetFlash 1GB.E01
Type: E01
Size(bytes): 1022361600
MD5: 83b9882d79e96f3b4a21b3a81b2e61cd
Sector Size: 512
Time Zone: America/New_York Acquisition Details
Description: BARBER JetFlash 1GB
Evidence Number: BARBER JetFlash 1GB
Examiner Name: delme
Model: TS1GJFV20
Serial Number: C1S0S5QK
Device Label: JetFlash
Acquired Date: Wed Nov 9 09:48:03 2016
System Date: Thu Oct 15 03:35:42 2015 Acquiry Operating System: Windows 10
Acquiry Software Version: 8.01.00.50
Device ID: 850ef81e-4840-4c70-a720-75a4fbe1465e
Internal ID: 746745
Name: /img_AVENAL SanDisk Cruzer Micro.E01
Type: E01
Size: 2055021056
MD5: 518dd322f8a532b688ac52fc238a8f76
Sector Size: 512
Time Zone: America/New_York Acquisition Details
Description: AVENAL SanDisk Cruzer Micro Evidence Number: AVENAL SanDisk Cruzer Micro Examiner Name: delme
Model: U3 Cruzer Micro
Serial Number: 000018DA860F6F9
Device Label: SanDisk
Acquired Date: Wed Nov 9 10:04:16 2016
System Date: Thu Oct 15 03:28:03 2015 Acquiry Operating System: Windows 10
Acquiry Software Version: 8.01.00.50
Device ID: 5c37b3ba-4f9e-471e-b3a5-0d5136323895
Internal ID: 746645
Name: IRRIDIUM-DC Logical Acq.L01
Type: E01
Size(bytes): 13269732
MD5: 9a404a157f103c7175456c1d2a259e0e
SHA1: 98b223d4e35329509feec213d655891ce46e6b7f
SHA-256: 167243cae57ef8ffdb73d1adbbdfa1f0472217f861f63ffc1aa7e7e62d849efd Sector Size: 4096
Time Zone: America/New_York Acquisition Details
Description: IRRIDIUM-DC Logical Acq
Examiner Name: delme
Acquired Date: Thu Jan 1 00:00:00 1970
System Date: Thu Jan 1 00:00:00 1970 Acquiry Operating System: Windows 10
Acquiry Software Version: 8.01.00.50
Device ID: 424f0bed-c00a-4e88-b913-2a18452c6309
Internal ID: 747984
NAME: IRRIDUM-BARBER Memory.bin
Device: RAM
Type: Local
MIME Type: application/octet-stream
Size(bytes): 2147483648
File Name Allocation: Allocated Metadata Allocation: Allocated
MD5: ef102186924e7fed24bc6d3bbbea4ec1
SHA-256: 99690f493850b864bf7365cd729860008f95a45da223ec74855f2bfd96122706
Hash Lookup Results: UNKNOWN Internal ID: 747787
Name: IRRIDUM-AVENAL Memory.bin
Device: RAM
Type: Local
MIME Type: application/octet-stream
Size(bytes): 2147483648
File Name Allocation: Allocated Metadata Allocation: Allocated
MD5: 45fa8429d76ea2a78f2e5906359a39d8
SHA-256: 7d45044f2ca4ecd2c0f8c6af65f91860a6547d31905413f287e9f6035c3e96a4
Hash Lookup Results: UNKNOWN Internal ID: 747784
Investigation Report
Using Autopsy, Prefetch Parser, ShellBagsView, JumpListsView, USB Forensic Tracker, and ShadowCopyView, investigate any claimed data theft/unauthorized host intrusion, as well as any criminal conduct performed by Avenal before he was fired.
Ismael Belem, a digital forensic & incident response investigator, conducted a forensic assessment of the preserved material. Each image was mounted with autopsy, and the vhd files were mounted with Arsenal image mounter, from which we were able to get the Avenal-encrypted image using the BitLocker recovery password.
We ran Autopsy 4.18.0 and parsed the file that our IT security staff had uploaded to the server. We started our inquiry by analyzing image by image and looking for evidence.
We started our investigation by examining the image IRRIDIUM-AVENAL.E01. We noticed that while Barber was away the other day, Richmond Avenal wrote her an email on October 5, 2015, at 06:48:43 EDT indicating that the IT staff had installed TeamViewer on her computer. If any pop-up messages appear on her screen, she shouldn’t be alarmed.
From: Richmond Avenal [mailto:richmond.avenal@irridium.local] Sent: Monday, October 5, 2015 11:49 AM
Subject: TeamViewer
Hi Jen
Just a reminder that IT installed TeamViewer on your computer while you were out the other day. If you see any pop-up messages about it you don’t need to worry.
Best.
Richmond
Barber also wrote Avenal an email on 10/05/2015 at 11:59 AM in which she shared a photo of herself and her children on vacation and even mentioned the names of her children.
To: Jen Barber <jen.barber@irridium.local>
From: Richmond Avenal <richmond.avenal@irridium.local> Subject: RE: Time Off
Date: Thu, 8 Oct 2015 10:37:28 +0100
Importance: normal
X-Priority: 3 In-Reply-To:
<F0674C7A-4562-4572-BAEC-B16CC49EAF15@irridium-dc.irridium.local> References:
<F0674C7A-4562-4572-BAEC-B16CC49EAF15@irridium-dc.irridium.local> Content-Type: multipart/alternative;
boundary="_15FF86D0-1837-4B2B-96CC-1B1DCF948E10_"
--_15FF86D0-1837-4B2B-96CC-1B1DCF948E10_
Content-Transfer-Encoding: quoted-printable Content-Type: text/plain; charset="utf-8" OK. See you later.
Richmond
Sent from Mail for Windows 10 From: Jen Barber
Sent: Thursday, October 8, 2015 10:35 AM To: richmond.avenal@irridium.local Subject: Time Off
Richmond,
I=E2=80=99m taking a few hours off to see Dora & Gwen=E2=80=99s school play=
. Shouldn=E2=80=99t be more than a couple of hours. Sent from Mail for Windows 10
You've just got to work harder!
From: Richmond Avenal [mailto:richmond.avenal@irridium.local] Sent: Monday, October 5, 2015 12:05 PM
To: 'Jen Barber' Subject: RE: Holiday
Incredible. Wish I had the money to go and see it. :( From: Jen Barber [mailto:jen.barber@irridium.local] Sent: Monday, October 5, 2015 12:01 PM
To: 'Richmond Avenal' Subject: RE: Holiday
Not sure what it's meant to signify, but believe it or not it's the same size as the thing on the top of St. Peter's Basilica!
From: Richmond Avenal [mailto:richmond.avenal@irridium.local] Sent: Monday, October 5, 2015 12:00 PM
To: 'Jen Barber' Subject: RE: Holiday Awesome.
What's that big globe thing?
From: Jen Barber [mailto:jen.barber@irridium.local] Sent: Monday, October 5, 2015 11:59 AM
To: 'Richmond Avenal' Subject: Holiday
Hey Richmond,
Here are a couple of pictures showing the Vatican trip. Dora&Gwen loved it!
Besides, Jen Barber also sent out an email to Richmond Avenal on October 5, 2015, at 07:03:55 EDT regarding titles of those strictly confidential quotes that Richmond Avenal was not allowed to access them, such as “Flower-Power Holdings, Fraggle Inc., Jenson Enterprises, and Weyland-Yutani”
We were able to locate a virtual hard disk called Stuff.vhd, located in /img_IRRIDIUM- AVENAL.E01/vol_vol3/Users/richmond.avenal/Documents/Stuff.vhd. When we mounted the virtual hard disk, we found out that the virtual hard disk was encrypted by BitLocker. However, we managed to unlock the virtual hard disk by using the recovery key (594858179674652850618948667656268378541156660748) that was provided by IT Security Staff.
After unlocking the Stuff.vhd, we can see there are four folders inside, which are Installers, PSTools, Quotes Downloaded October 8th, 2015 and Quotes Downloaded October 14th, 2015 . There are files inside each folder, and the files are listed as follows:
Installers: Eraser 6.2.0.2970.exe, filedatech.zip, fstouch64.zip, SDelete.zip and TeamViewer_Setup_en.exe
PSTools: PsExec.exe, psfile.exe, PsGetsid.exe, PsInfo.exe, pskill.exe, pslist.exe, PsLoggedon.exe, psloglist.exe, pspasswd.exe, psping.exe, PsService.exe, psshutdown.exe, pssuspend.exe
Quotes Downloaded October 8th, 2015: Flower-Power Holdings Inc. - October 2nd, 2015.docx, Flower-Power Holdings Inc. - October 2nd, 2015.pdf, Fraggle Inc. - October 2nd, 2015.docx, Fraggle Inc. - October 2nd, 2015.pdf, Jenson Enterprises - October 2nd, 2015.docx, Jenson
Enterprises - October 2nd, 2015.pdf, Weyland-Yutani - October 5th, 2015.docx and Weyland- Yutani - October 5th, 2015.pdf
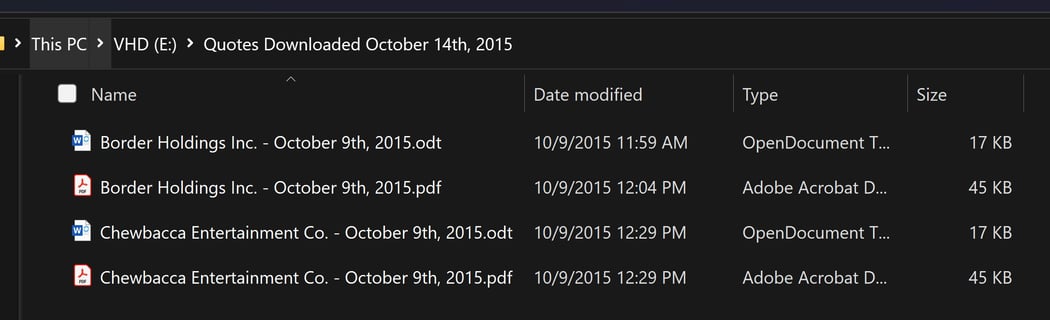
Quotes Downloaded October 14th, 2015: Border Holdings Inc. - October 9th, 2015.odt, Border Holdings Inc. - October 9th, 2015.pdf, Chewbacca Entertainment Co. - October 9th, 2015.odt, and Chewbacca Entertainment Co. - October 9th, 2015.pdf
As we can see, Richmond Avenal was not only to have access to those four confidential quotes that Jen Barber mentioned that he was not supposed to have access to, but he also had two additional quotes on his virtual hard disk (Border Holdings Inc. and Chewbacca Entertainment Co.). We also assumed that he had the intention to erase those confidential quotes and traces on the machine using Eraser 6.2.0.2970.exe, filedatech.zip, fstouch64.zip, SDelete.zip and PSTools.
Figure 1: Folders inside the Stuff.vhdFigure 5: Folders inside the Stuff.vhd
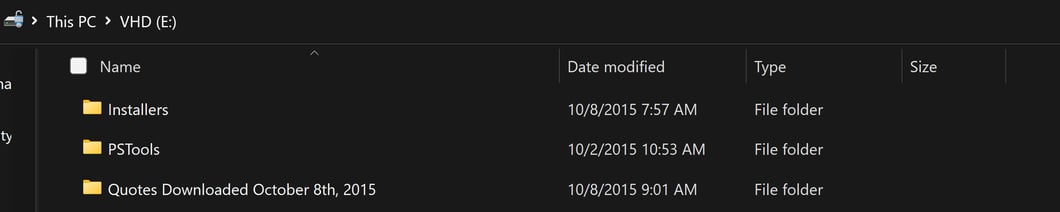
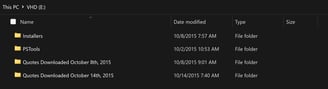
Figure 2: Quotes Downloaded October 8th, 2015
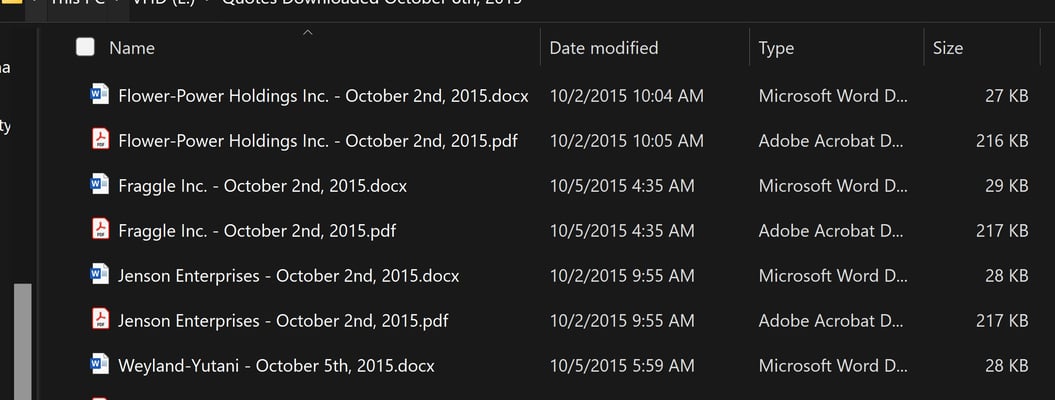
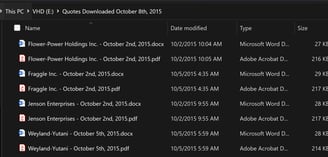
Figure 3: Quotes Downloaded October 14th, 2015
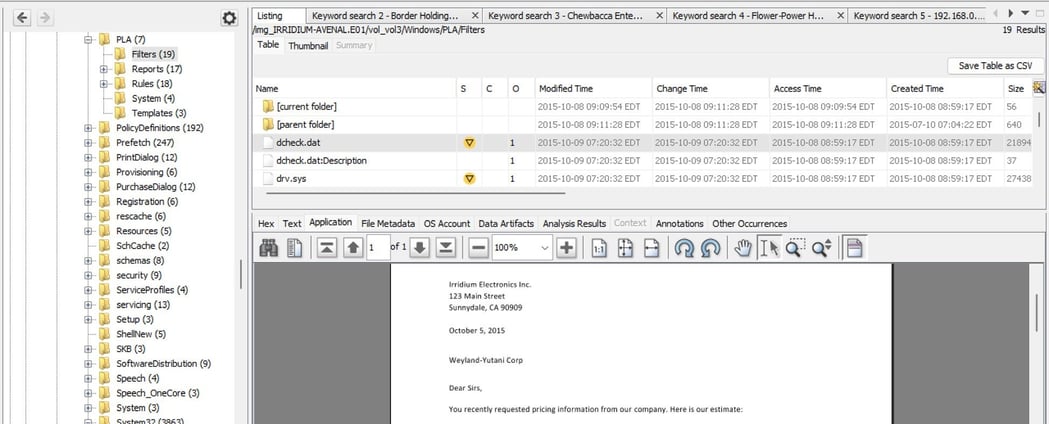
Moreover, we discovered that Richmond Avenal was trying to hide those confidential quotes with different names and extensions_located_at/img_IRRIDIUM-AVENAL.E01/vol_vol3/Windows/PLA/Filters.The files are listed below with the original names:
zlib64.dll = Weyland-Yutani - October 5th, 2015.docx dcheck.dat = Weyland-Yutani - October 5th, 2015.pdf
zlib.dll = Flower-Power Holdings Inc. - October 2nd, 2015.pdf drv.sys = Flower-Power Holdings Inc. - October 2nd, 2015.docx vdiff.zip = Jenson Enterprises - October 2nd, 2015.docx rmi.vxd = Jenson Enterprises - October 2nd, 2015.pdf pagedrv.sys = Fraggle Inc. - October 2nd, 2015.pdf
gdi.mon = Fraggle Inc. - October 2nd, 2015.docx
Figure 4: Confidential quotes with different names and extensions
By looking at the prefetch folder located at /img_IRRIDIUM- AVENAL.E01/vol_vol3/Windows/Prefetch, we can see that Richmond Avenal has TeamViewer installed on his machine. After looking at the TeamViewer log located_at_/img_IRRIDIUM-AVENAL.E01/vol_vol3/ProgramFiles(x86)/TeamViewer/Connections_incoming.txt, we can see there were multiple connections made by Richmond Avenal. The unique session id of the TeamViewer was 976000391. We also see that programs such as ERASER 6.2.0.2970.EXE, and SDELETE.EXE were running on the machine. These indicate that the user was trying to remove any evidence or trace on the machine.
Figure 5: Prefetch for teamviewer
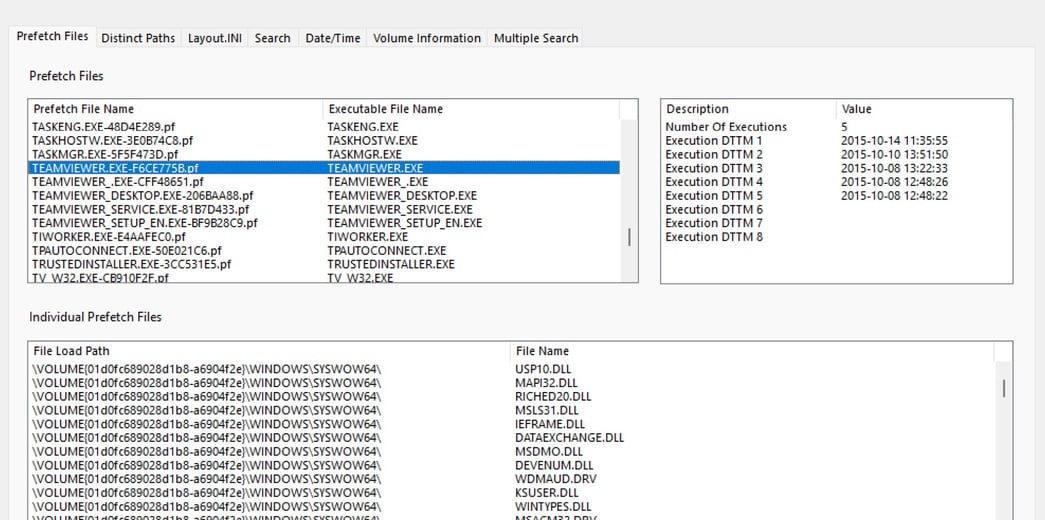
Figure 6: TeamViewer Connection
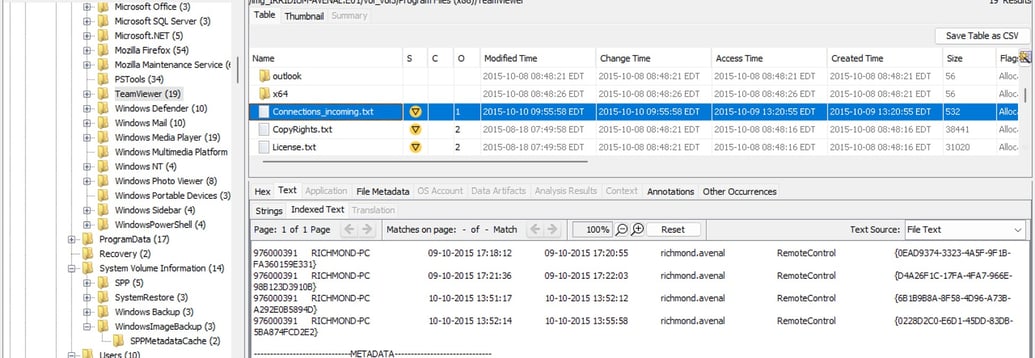
When we investigated the jumplist, we further confirmed that Richmond Avenal had access to those confidential quotes as well as the Stuff.vhd on his computer. We also discovered that Richmond Avenal had accessed Jen Barber’s folder name Quotes, where she saved all the confidential quotes, through the network. We also found that Richmond Avenal accessed the Barber’s TeamViewer log file.
Figure 7: JumpList regarding confidential quotes
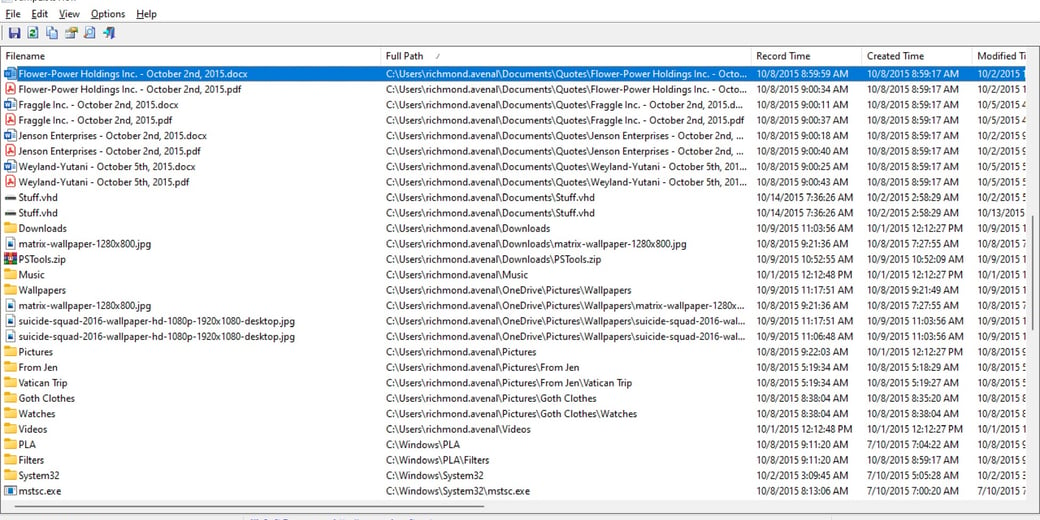
Figure 8: JumpList regarding accessing Barber folder through network
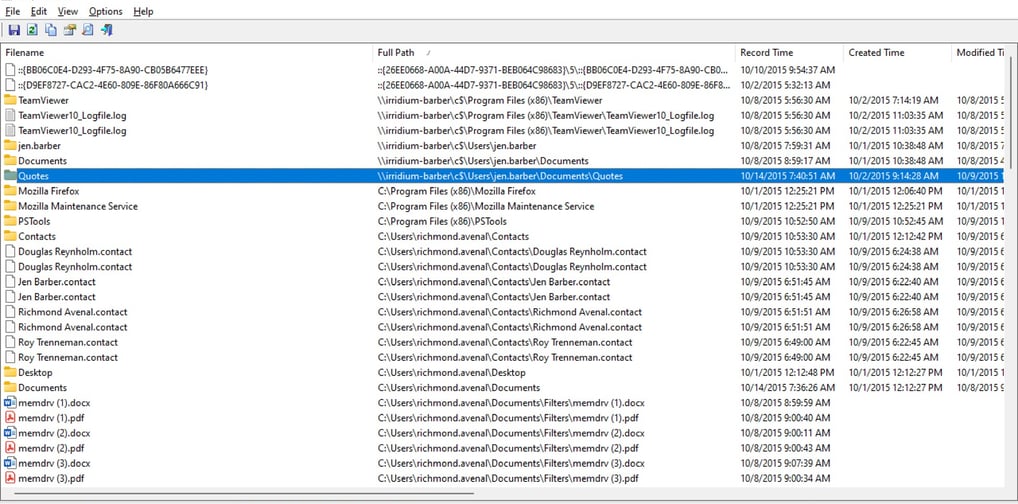
We also found that there were a couple of USB devices connected to Richmond Avenal’s computer. One of the USB devices is called SanDisk U3 Cruzer Micro USB Device. We further investigate the SanDisk U3 Cruzer Micro USB Device by mounting it on the Autopsy. We found that the USB device was encrypted by BitLockerToGo.
Figure 9: USB Forensic Tracker
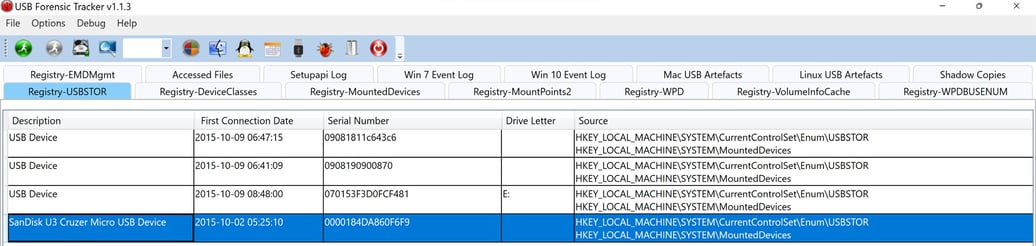
Figure 10: SanDisk U3 Cruzer Micro USB Device
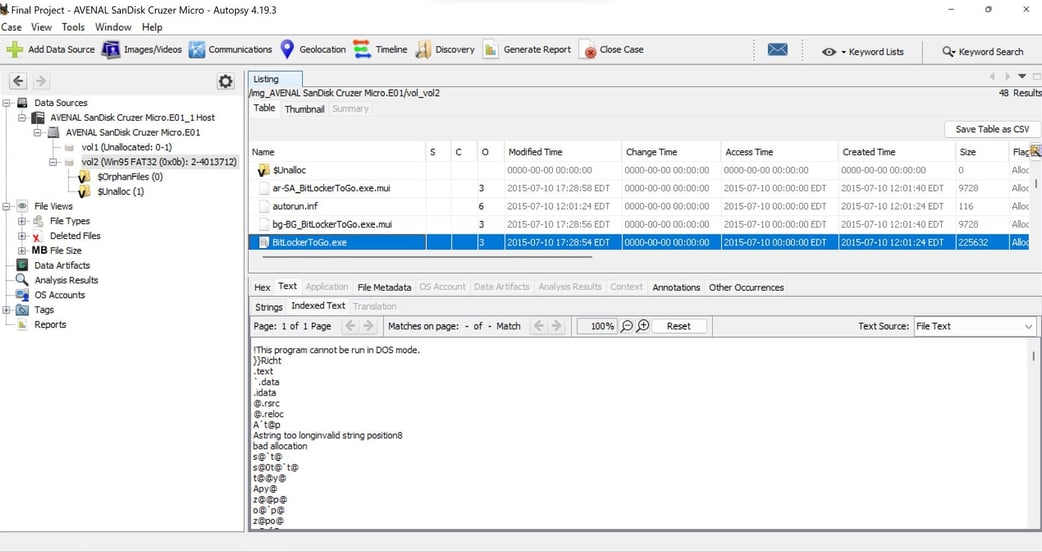
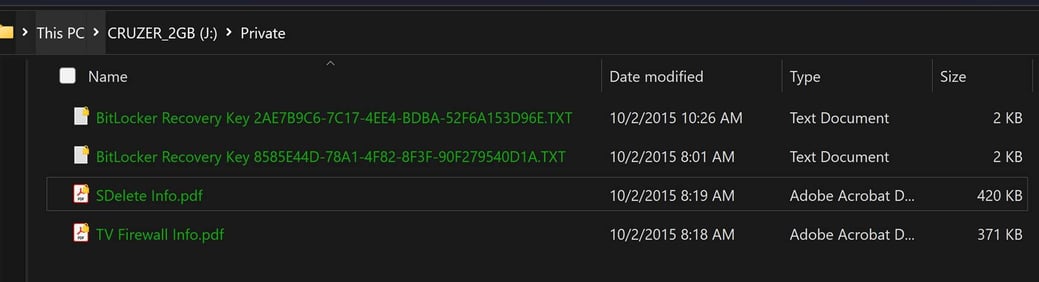
We managed to unlock it by using the recovery key (077407436876003740453519387629611215416295162514) that was provided by IT Security Staff. The USB device contains two folders which are Installers and Private. Installers folder contains Eraser 6.2.0.2970.exe, filedatech.zip, SDelete.zip, and TeamViewer_Setup_en.exe. The private folder contains two BitLocker Recover Keys, SDelete Info.pdf and TV Firewall Info.pdf.
However, the private folder is encrypted with the digital certificate by using the encrypting file system (EFS) feature on Microsoft. We managed to extract the digital certificate named Roy Trenneman - File Recovery Key.pfx on the IRRIDIUM-DCLogicalAcq.L01 image located in “/IRRIDIUM-DC Logical Acq.L01/IRRIDIUM-DC Logical Acq_1651611177109/LogicalEntries/C/Users/roy.trenneman/Documents/Encryption Keys/Roy Trenneman - File Recovery Key.pfx.” We installed the digital certificate on our forensic machine with the password “TryReb00ting” that was shared by a member of the IT Security team (Roy Trenneman). After opening the file SDelete Info.pdf, the user was trying to learn how to delete files in an unrecoverable way.
Figure 11: SanDisk U3 Cruzer Micro USB Device
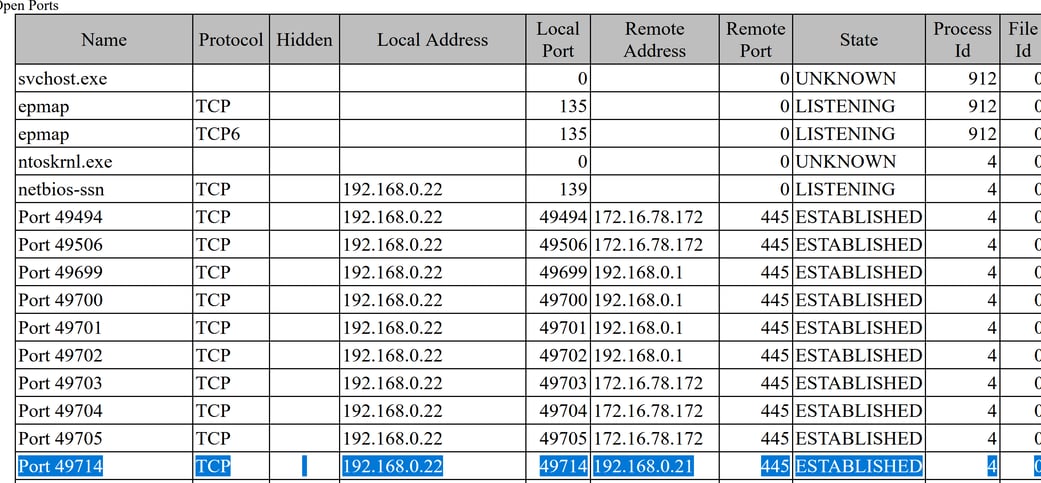
During our investigation of the snapshot of Richmond Avenal’s machine, We discovered that Avenal Workstation (192.168.0.22) made a remote connection with Jen Barber’s Workstation (192.168.0.21) by evaluating the remote port 445 (SMB). Server Message Block (SMB) protocol is a network file-sharing protocol that allows applications on a computer to read and write to files and to request services from server programs in a computer network.
Figure 12: Snapshot for Avenal (SMB port)
Avenal Workstation made a TCP connection using port 5938, according to the snapshots. The TeamViewer connection uses port 5938. Avenal’s IP address created a TeamViewer connection with the IP addresses 188.172.219.35 and 37.252.231.5, according to the snapshot.
Figure 13: Snapshot for Avenal (TeamViewer port)

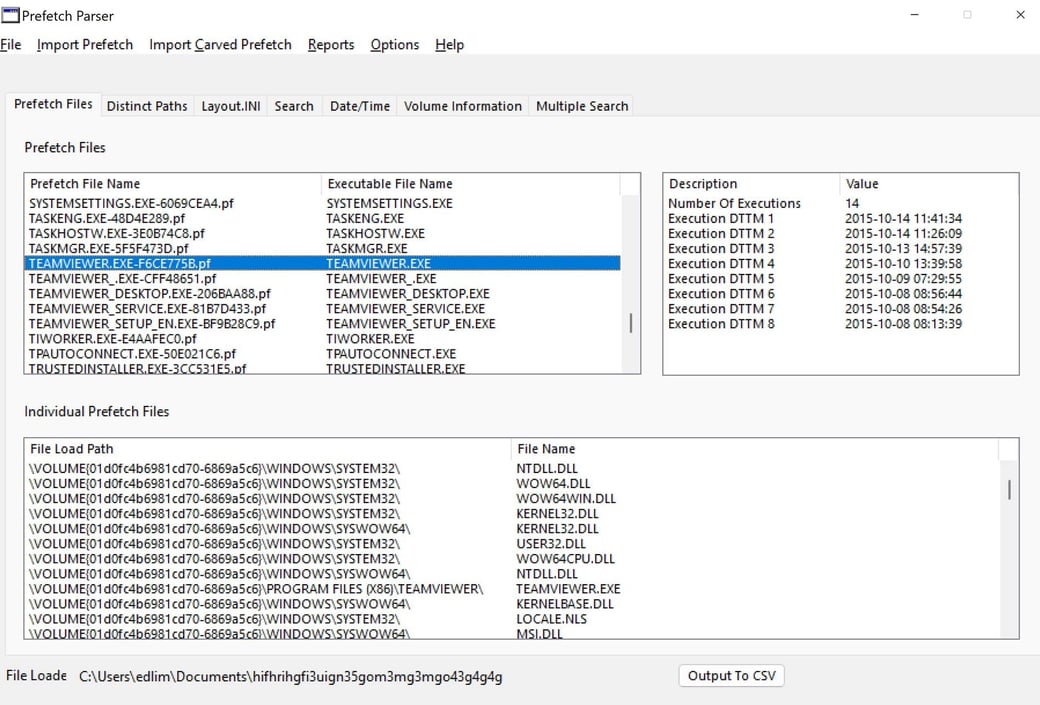
We proceed with our next investigation by examining the image IRRIDIUM-BARBER.E01. We found that the TeamViewer ran on Barber’s machine 14 times, and the last run happened on 2015-10-14 at 11:41:34 EDT. In addition, we found that SDelete was also running on Barber’s machine 13 times. We assume that Richmond Avenal might be remoting Barber’s machine using TeamViewer and ran SDelete to remove some of his traces on Barber’s machine.
Figure 14: TeamViewer ran on Barber’s machine
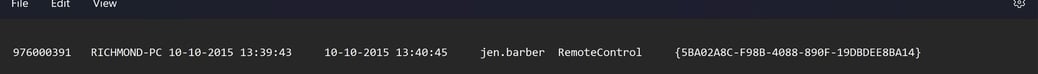
We further investigated Barber’s machine and found that the Connections_incoming.txt log file for TeamViewer did not exist. However, we were able to recover the log file by using the ShadowCopyView. We found that the unique session id 976000391 used for the established connection while using TeamViewer was the same as the log we found on Richmond Avenal’s machine. Therefore, we can further confirm that Richmond Avenal also used TeamViewer to remote into Barber’s machine without any permission.
Figure 15: ShadowCopyView on Barber’s machine
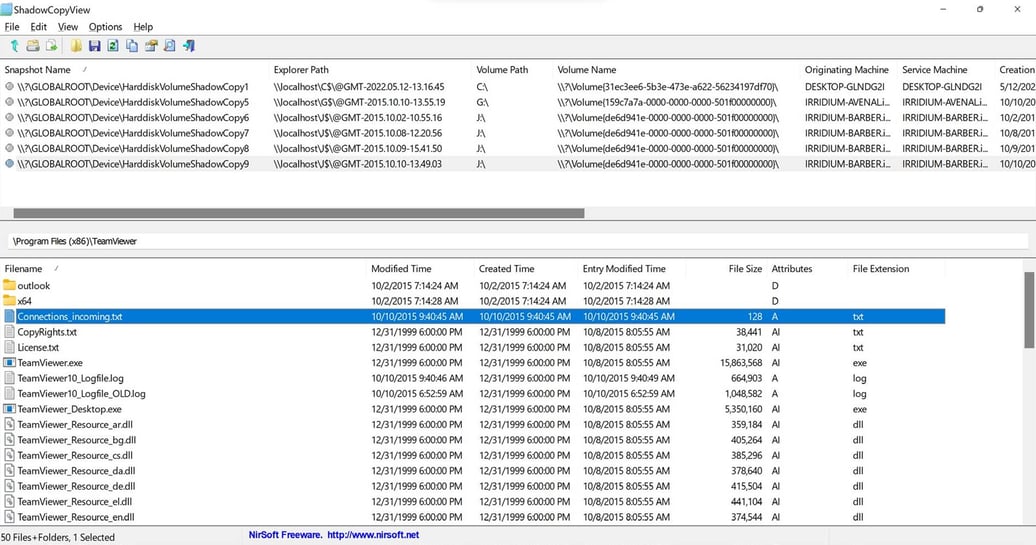
Figure 16: Incoming TeamViewer connection log on Barber’s machine
Moreover, we examined the snapshot for Barber’s machine. By assessing the remote port 445 (SMB) and the name microsoft-ds, we learned that Jen Barber’s Workstation (192.168.0.21) created a remote connection with Avenal Workstation (192.168.0.22). We can also see that the snapshot showed Barber’s machine also opened the TeamViewer port (5938).
Figure 17: Snapshot on Barber’s machine regarding SMB protocol
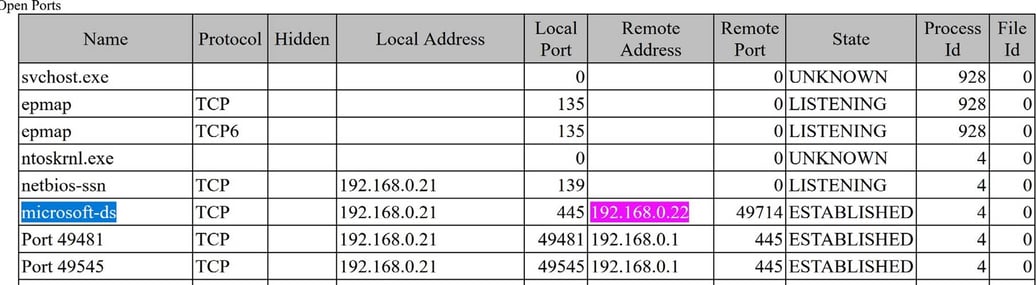
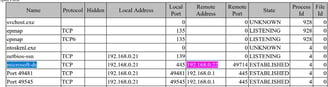
Figure 18: Snapshot on Barber’s machine regarding TeamViewer protocol

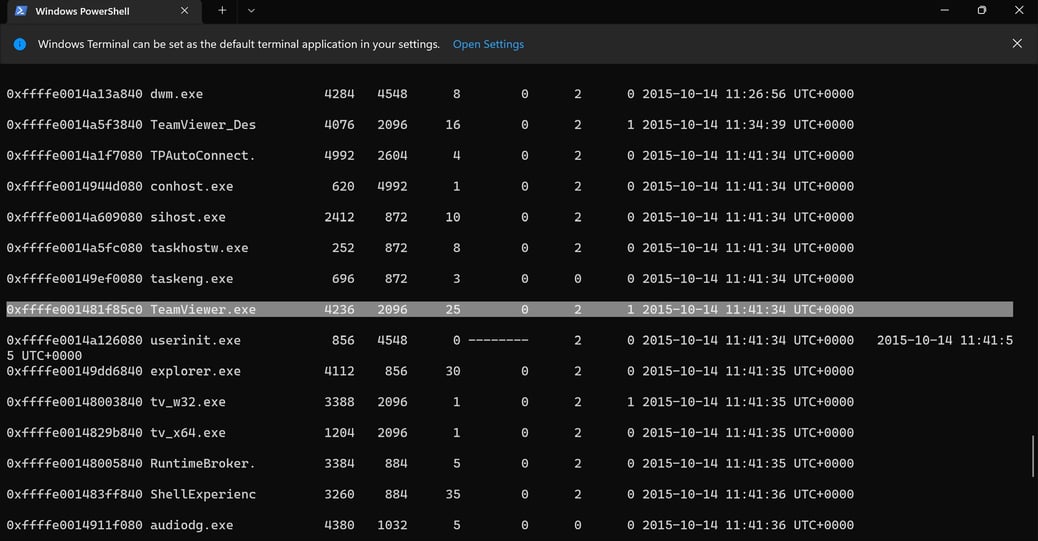
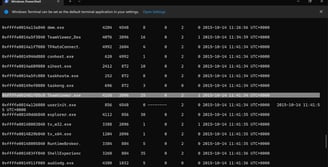
Furthermore, we inspected the RAM on Barber’s machine using volatility. We found that the TeamViewer was running at the moment the image was taken.
Figure 19: Volatility on Barber’s machine
CONCLUSION
A significant number of pieces of evidence were evaluated in total, with some proving interaction between Avenal and the rival company "Goth2Boss." We also discovered tangible proof that Avenal gained remote access to Barber's computer without her knowledge and took a confidential document. According to the data acquired, Barber's belief that Avenal was behind this behaviour based on a TeamViewer was probably true. This is not a piece of advice to be taken lightly.
IRRIDIUM-AVENAL
> 2015-10-01 11:50:02 EDT --> Default accounts on the system are created.
> 2015-10-02 02:58:29 EDT --> Stuff.vhd is created.
> 2015-10-02 02:58:43 EDT --> Last accessed on Stuff.vhd.
> 2015-10-02 07:09:53 EDT --> SDELETE.EXE last run.
> 2015-10-05 06:48:43 EDT --> Richmond Avenal sends an email to jen.barber@irridium.local regarding the installation of TeamViewer on her PC.
> 2015-10-05 06:58:39 EDT --> Jen Barber sends an email to richmond.avenal@irridium.local regarding her children Dora&Gwen.
> 2015-10-05 07:03:55 EDT --> Jen Barber sends an email to richmond.avenal@irridium.local regarding the titles of confidential quotes.
> 2015-10-08 07:59:29 EDT --> Last accessed on irridium-barberc$Usersjen.barber
> 2015-10-08 08:59:17 EDT --> Last accessed on Weyland-Yutani - October 5th, 2015.docx.
> 2015-10-08 08:59:17 EDT --> Last accessed on Flower-Power Holdings Inc. - October 2nd, 2015.pdf.
> 2015-10-08 08:59:17 EDT --> Last accessed on Jenson Enterprises - October 2nd, 2015.docx.
> 2015-10-08 08:59:17 EDT --> Last accessed on Jenson Enterprises - October 2nd, 2015.pdf.
> 2015-10-08 08:59:17 EDT --> Last accessed on Fraggle Inc. - October 2nd, 2015.pdf.
> 2015-10-08 08:59:17 EDT --> Last accessed on Fraggle Inc. - October 2nd, 2015.docx.
> 2015-10-08 08:59:17 EDT --> Last accessed on Flower-Power Holdings Inc. - October 2nd, 2015.docx
> 2015-10-08 08:59:17 EDT --> Last accessed on Weyland-Yutani - October 5th, 2015.pdf.
> 2015-10-8 9:01:23 EDT --> Last accessed on Quotes Downloaded October 8th, 2015.
> 2015-10-09 12:29:48 EDT --> Last accessed on irridium- barberc$Usersjen.barberDocumentsQuotes.
> 2015-10-14 7:40:51 EDT --> Last accessed on Quotes Downloaded October 14th, 2015.
> 2015-10-14 11:35:55 EDT --> TeamViewer.exe last run.
> 2015-10-08 09:15:16 EDT --> ERASER 6.2.0.2970.EXE last run.
IRRIDIUM-BARBER
> 2015-10-01 08:21:16 EDT --> Default accounts on the system are created.
> 2015-10-08 09:46:48 EDT --> SDelete.exe last run.
> 2015-10-10 9:40:45 EDT --> Connections_incoming.txt last modified time.
> 2015-10-14 11:41:34 EDT --> TeamViewer.exe last run.
TIMELINE Of EVENTS
HashMyFiles v2.43
Autopsy v4.19.3
FTK Imager v3.4.3.3
USB Forensic Tracker v1.1.3
Prefetch Parser v2.0.0.9
ShellBagsView v1.30
JumpListsView v1.16
ShadowCopyView v1.15
Volatility v2.5
LIST OF TOOLS USED
1. ACCESSDATA. (2022, Jan 21). FTK Imager Version 4.7.1. https://accessdata.com/product-download/ftk-imager-version-4-7-1, visited 05/02/2022 at 2 PM EST.
2. AUTOPSY DIGITAL FORENSICS. AUTOPSY. https://www.autopsy.com/download/, visited 05/02/2022 at 2 PM EST.
3. Belkasoft. Forensic Analysis of LNK Files. https://belkasoft.com/forensic-analysis-of-lnk-files, visited 05/02/2022 at 3 PM EST.
4. Markmckinnon. (2016, Oct 27). Prefetch_Parser. https://github.com/markmckinnon/Prefetch_Parser, visited 05/02/2022 at 3 PM EST.
5. NirSoft. JumpListsView v1.16 - View jump lists information stored by Windows 7 Copyright(c) 2013 - 2018 Nir Sofer. https://www.nirsoft.net/utils/jump_lists_view.html, visited 05/02/2022 at 2 PM EST.
6. NirSoft. ShadowCopyView. https://www.nirsoft.net/utils/shadow_copy_view.html, visited 05/02/2022 at 2 PM EST.
7. NirSoft. ShellBagsView v1.30 Copyright (c) 2008 - 2020 Nir Sofer. https://www.nirsoft.net/utils/shell_bags_view.html, visited 05/02/2022 at 2 PM EST.
8. VOLATILITY FOUNDATION. Volatility. https://www.volatilityfoundation.org/, visited 05/02/2022 at 2 PM EST.
9. Orion Forensics Lab. USB Forensic Tracker. http://www.orionforensics.com/forensics-tools/usb-forensic-tracker/, visited 05/02/2022 at 2 PM EST.
REFERENCES